Authentication Mechanisms of the ADOIT Web Client
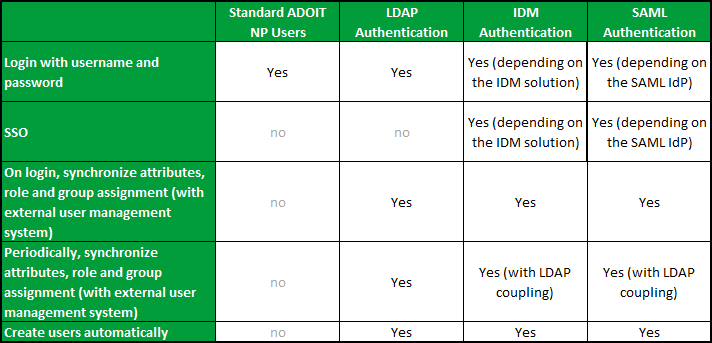
This part of the manual contains an overview of the different authentication mechanisms of the ADOIT web client. The authentication mechanisms can be used separately or in combination.
Standard ADOIT Users
ADOIT users
are created in the Administration Toolkit.
Login to the ADOIT web client requires input of username and password. These credentials are used to authenticate the user against the available data in the ADOIT database.
The assignment of user attributes, rights and system roles are controlled via the User Management component in the Administration Toolkit.
For instructions on how to create ADOIT users, see the chapter User Management in the Administration Manual.
LDAP Authentication
Users can either be imported from a directory service or mapped to ADOIT users.
Login to the ADOIT web client requires input of username and password. The provided credentials will be used to authenticate the user against the configured directory service.
A precondition for this scenario is that the connection of ADOIT to the directory service in use (e.g. Active Directory) is established on the Admin Page.
The assignment of user attributes, rights and system roles may be controlled via the User Management component in the Administration Toolkit or synchronised with an external directory service.
Specific configuration steps are necessary when setting up the ADOIT web client for this authentication mechanism. For instructions, see the chapter Set Up Web Client Login with LDAP Coupling.
IDM Authentication
Users can either be imported from an external user management system or mapped to ADOIT users.
Login to the ADOIT web client via single sign-on is possible using an Identity Management System (IDM).
A precondition for this scenario is the connection of ADOIT to an authentication server in the target environment which provides means for authentication with an external user management system (e.g. Microsoft Internet Information Services connected to an Active Directory).
The assignment of user attributes, rights and system roles may be controlled via the User Management component in the Administration Toolkit or synchronised with an external user management system.
Specific configuration steps are necessary when setting up the ADOIT web client for this authentication mechanism. Please contact your ADOIT consultant to receive instructions.
SAML Authentication
Users can either be imported from an external user management system or mapped to ADOIT users.
The external user management system must provide an Identity Provider (IdP) for SAML 2.0 (e.g. Active Directory Federation Services [AD FS] or Shibboleth).
To log on to the web client, the user is redirected to the IdP. Depending on the configuration of the IdP, the authentication is carried out via single sign-on or by entering access data (username and password, certificates, etc.).
No server-to-server communication is necessary for this authentication mechanism, since all data is transmitted via the browser.
The assignment of user attributes, rights and system roles may be controlled via the User Management component in the Administration Toolkit or synchronised with an external user management system.
Specific configuration steps are necessary when setting up the ADOIT web client for this authentication mechanism. Please contact your ADOIT consultant to discuss the integration process.